Overlords: Part 7. The Export Layer — Runtime Governance Goes Global
What began as trauma-coded control is now an administrative default. The stack is live. The refusal isn’t obvious.
The Overlords sequence has tracked a single system through its successive disguises—politics as theatre, governance as protocol, consent as conditional access. Early instalments mapped the replacement of representation with layered compliance logic, the rise of soft law over constitutional authority, and the fusion of identity systems with biological gatekeeping. Part 1 exposed electoral theatre as scripted compliance. Part 2 mapped the layered logic of behavioural enforcement. Part 3 detailed soft law's override of sovereignty. Part 4 tracked the conversion of identity into access. Part 5 revealed the genetic gating of the human subject.
Part 6 shifted focus from static architecture to live trials, showing how distinct regimes acted as laboratories for control: mass industrial discipline, permissioned prosperity, and legible micromodel governance. Each yielded artefacts stripped of their original ideological skins, ready to be redeployed in other contexts. What was once bound to specific histories now exists as a transferable runtime logic.
That is the point of departure here. The prototypes have dissolved into the environment. The system is no longer in design phase—it is operational.
Introduction: From Protocol to Deployment
The closed-loop controls trialled in the testbeds of Part 6 were not isolated experiments; they were prototype environments for export. What proved durable under constrained conditions—identity-linked access, integrated data governance, compliance-driven eligibility—now forms the operational grammar of the export layer.
The control stack now runs as a live layer in global governance. Its modules—compliance infrastructures for health, finance, surveillance, and sustainability—interlock without reference to the political traditions in which they were first trialled. The apparatus has shed its dependence on revolutionary myth or electoral legitimacy; it functions through metrics, access controls, and institutional harmonisation.
This is not a hidden conspiracy. The architecture is visible, routinised, and defended as administrative necessity. The point of integration is technical, not ideological: disparate jurisdictions mesh through shared standards, credentialing regimes, and data pipelines. The optics of politics remain, but the theatre has been relegated to brand maintenance. The governing logic is execution, not persuasion—services delivered, signals monitored, compliance inferred from the absence of interruption.
The UAE’s governance model now exports through formal state partnerships and informal broker networks, with figures like Tony Blair serving as conduits between local administrative logic and global compliance systems.
The Control Stack Goes Global
The present governance lattice is modular by design. Health, finance, surveillance, and sustainability no longer operate as separate policy arenas; they are interdependent sub-systems feeding the same conditional access framework. A vaccination certificate doubles as a travel permit. Banking compliance requirements trigger data handshakes with health registries and biometric ID platforms. Environmental, social, and governance (ESG) metrics—originally corporate disclosure tools—now function as jurisdictional filters, determining market participation or exclusion. The modules are technically discrete yet architecturally fused, enabling upgrades in one domain to propagate across the entire stack without public deliberation.
In this configuration, control logic is stripped of ideological content. Integration proceeds not by persuading populations of a grand narrative, but by embedding obligations into interoperable systems. Compliance becomes a matter of passing a checksum—meeting the required data standard, furnishing the right credential—rather than demonstrating political loyalty. The enforcing principle is procedural: an incomplete profile, an outdated credential, or a mismatched data point can quietly revoke access without a single overt prohibition.
Conditionality is no longer framed as punishment or exclusion, but as the price of safety, equity, and resilience. Each term is elastic, functioning as a semantic cover for pre-emptive governance. A payment system’s fraud protection doubles as political risk management. Carbon reporting requirements, presented as environmental safeguards, extend into supply-chain policing and credit allocation. Public health campaigns morph into durable population-mapping exercises. The stated goals are protective; the operative outcomes are permissioned participation.
The older Cold War frame—opposing ideological blocs, each with its own economic model—is obsolete in this schema. What has replaced it is a mesh of interoperable systems, each capable of docking into the other’s compliance protocols. Banking standards flow from Basel to Shanghai; biometric templates align across NATO and BRICS; climate disclosure frameworks adopted by Western multinationals slot directly into Gulf sovereign wealth portfolios. The effect is not homogenisation into a single political identity, but convergence into a shared runtime where control is exerted through compatibility requirements, not ideological conversion.
Institutional Layer: The Harmonisation Engine
At the top of the integration chain sit institutions whose stated functions mask their role as protocol synchronisers. The World Economic Forum (WEF), World Health Organization (WHO), International Monetary Fund (IMF), and United Nations (UN) are not identical in mandate, but they operate as harmonisation engines—defining standards, aligning metrics, and ensuring that local systems can be slotted into a global compliance grid. Their authority does not rest on direct sovereignty but on the ability to set interoperability conditions that states, corporations, and NGOs must meet to remain inside the system’s flow.
Frameworks like the Sustainable Development Goals (SDGs), Environmental, Social, and Governance (ESG) metrics, and the emerging Pandemic Treaty serve as programmable governance schemas. Each functions as a soft-law API: formally non-binding, yet materially compulsory for access to funding, trade, or institutional legitimacy. They translate political aims into measurable indicators, which in turn become operational prerequisites. Once adopted, these schemas are versioned, updated, and enforced not through parliaments or plebiscites, but through funding cycles, procurement standards, and platform terms of service.
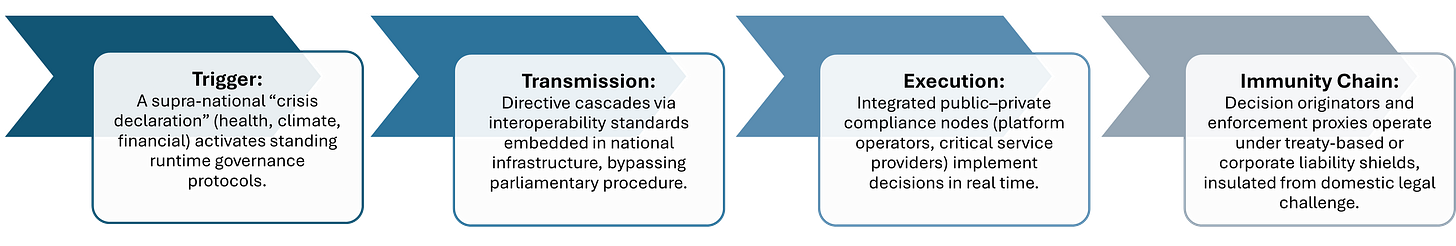
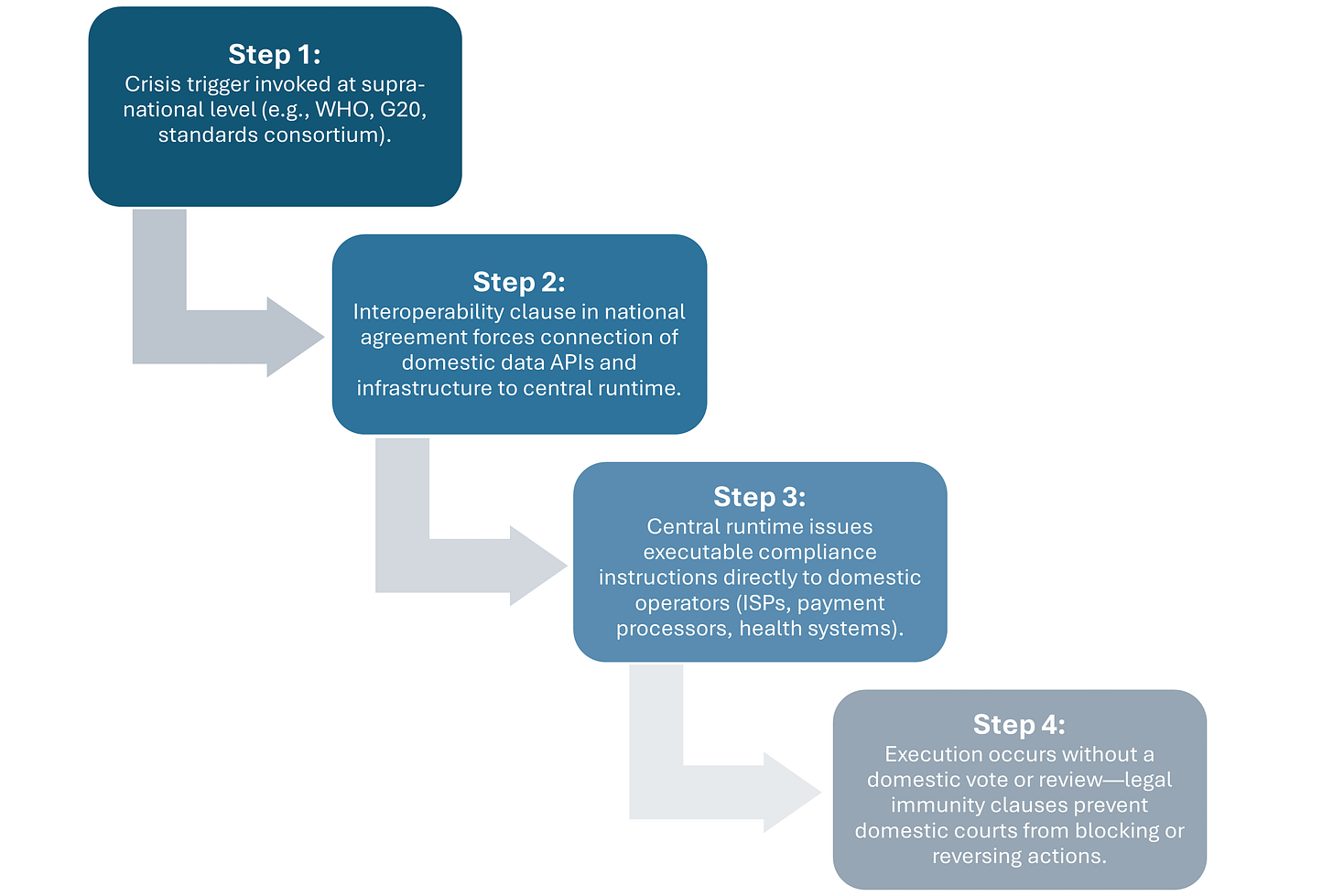
Two examples illustrate how governance triggers in one policy domain are used to activate enforcement in entirely different sectors:
Relay 1 — WHO Crisis Trigger → AI Governance Compact
The WHO’s public health emergency trigger auto-activates cross-sector that now include AI model governance. This allows AI output filtering and content suppression to be enforced as a public health measure, even when the underlying AI ruleset was drafted under unrelated compacts.Relay 2 — Climate Emergency → Digital ID Mandate
A declared climate emergency activates energy rationing frameworks which require real-time personal carbon tracking. That tracking is enabled only through the existing digital ID infrastructure—originally implemented for financial inclusion and pandemic access control—creating a direct operational bridge between climate policy and identity governance.
This produces multi-scalar integration: jurisdictional nesting replaces national divergence. Municipal climate policies align with national carbon reporting, which in turn maps directly onto global emissions registries. Public health protocols cascade from WHO guidance to regional regulatory frameworks to local enforcement without requiring ideological alignment. A city can comply with global governance standards while its national government maintains a nominally antagonistic political stance—the protocol routes through the administrative backplane.
The ideological cover for this process is stakeholderism, often reinforced by communitarianism—the doctrine that individual rights must be balanced, and often subordinated, to the perceived needs of the collective. In operational terms, communitarian framing provides the moral pretext for embedding conditionality into access systems: restrictions are recast as rather than coercion. This makes standardisation appear as civic duty, enabling population-wide compliance without open contestation.
The intellectual and political lineage is not accidental. A network of policy-shaping organisations and elite forums operate as upstream code-writers for governance standards, including:
Fabian Society – Founded 1884 in Britain, committed to gradualist, elite-led reform rather than revolutionary change. Embedded deeply in socialist and Labour Party politics, supplying ministers, civil servants, and policy advisers. Advances communitarian framing and technocratic planning within ostensibly democratic systems.
Chatham House (Royal Institute of International Affairs) – Founded 1920 as a British counterpart to the US Council on Foreign Relations. Serves as a closed-door forum for elite policy convergence in foreign affairs, trade, and governance standards. Produces frameworks later formalised by states and multilateral bodies.
Council on Foreign Relations (CFR) – US-based, established 1921, with deep integration into finance, defence, and diplomatic sectors. Shapes long-range policy positions and aligns US corporate, military, and political interests with global governance architectures.
Trilateral Commission – Founded 1973 by David Rockefeller and Zbigniew Brzezinski to link North America, Western Europe, and Japan in coordinated policy. Promotes — a stakeholderism analogue at geopolitical scale — and supplies senior personnel to governments, central banks, and global agencies.
Mont Pelerin Society – Formed 1947 by Friedrich Hayek and allied economists to entrench neoliberal orthodoxy. Functionally parallel to Fabian gradualism in method—networked academia, think tanks, and elite retreats to set policy baselines—despite ideological contrast.
Tavistock Institute & Related Behavioural Science Bodies – Originated in British military psychiatry, later pivoting to social engineering in organisational, educational, and media contexts. Designs behavioural conditioning frameworks later deployed via public policy or corporate governance.
Club of Rome – Founded 1968; advanced sustainability as a planetary governance priority via Limits to Growth. Supplied the conceptual basis for climate-linked governance schemas later embedded in SDGs and ESG metrics.
These bodies differ in stated ideology and membership base, yet functionally converge on the same outcome: replacing overt political contest with pre-formatted governance templates. The optics are participatory; the architecture remains technocratic, credential-gated, and self-reinforcing.
Credential over Consent: Rise of the Transnational Noocracy
Authority in the converged governance environment no longer routes through the voter; it routes through the validator. The decisive act is not casting a ballot but presenting an approved credential that satisfies the system’s compatibility checks. Electoral cycles still occur, but they are vestigial interfaces—ritual affirmations running in parallel to the real legitimacy engine, which operates through verified compliance with technical, professional, and behavioural standards.
Across regimes with otherwise incompatible political branding, the underlying equation is constant: credential + compliance = legitimacy. Whether in a single-party technocracy, a European parliamentary democracy, or a Gulf monarchy, the governing stratum draws authority from its ability to demonstrate alignment with system metrics—public health dashboards, financial compliance records, ESG scores, or security clearances. The credential is not merely proof of capacity; it is a licence to participate in the administrative core. Without it, access to influence collapses, regardless of formal rights.
This credentialism masks command logic in the garments of soft law. Qualification frameworks, professional licensing, and standards certification present as neutral, technical safeguards, yet they determine who is permitted to design, interpret, and enforce governance schemas. A climate negotiator without the sanctioned institutional backing, a doctor without the approved public health accreditation, or a financier outside compliance regimes is structurally excluded from decision-making channels, however persuasive their argument or popular their support.
The concept of a ruling persists, but its source has shifted. It is no longer a metaphysical grant, as in divine right, nor the statistical claim of a democratic majority. In the transnational noocracy, the Mandate is conferred by signal fidelity—the capacity to demonstrate, through continuous data outputs, that one’s operations are aligned with the metrics of system stability and policy orthodoxy. It is a live, performance-based legitimacy: fall out of alignment, and the Mandate dissolves, not through revolution or election, but by administrative disconnection.
Case Study: UAE — Runtime Stack in Full Deployment
The UAE operates without democratic mandate yet exemplifies runtime governance—integrated across biometrics, fintech, surveillance, and digital identity. The UAE Pass platform serves as a unified digital ID used by over 11 million individuals to access more than 5,000 public, semi-governmental, and private services via one login, digital signatures, and facial recognition. The Emirates ID card, mandatory for all residents, embeds biometric data and microchip-based identity for authentication across both government and private sectors. Financial institutions must adhere to biometric identity verification and e‑KYC procedures in line with Central Bank regulations.
The UAE has adopted cutting-edge surveillance tools, some sourced from or modelled on Israeli cyberintelligence capabilities, operating at scale domestically. It simultaneously pursues partnerships with China to bolster AI, infrastructure, and enterprise integration (a $5 billion collaboration on AI and infrastructure, for example). At the same time, the approach to fintech and sustainability deploys Western-aligned ESG frameworks—blockchain-backed payments, green finance, and digital innovation conforming to global standards—all aligned with the UAE’s Net Zero by 2050 strategy.
Formal diplomatic acts like the Abraham Accords—which opened ties between the UAE and Israel—function less as normative shift and more as technological and administrative fusion. What appears as dissolves into data-sharing, surveillance interoperability, and collaborative infrastructure systems.
Former UK Prime Minister Tony Blair has served as a direct transmission channel between Western political capital and Gulf runtime governance. His post-office consultancy, Tony Blair Associates, embedded staff in Abu Dhabi under multimillion-dollar contracts, offering the UAE access to a curated network of global political figures, policy technocrats, and corporate partners. This was not transactional lobbying but structural advisory—aligning domestic administrative reforms with international compliance and performance frameworks. The later Tony Blair Institute for Global Change formalised this role, lobbying and advising the UAE on governance strategy, data-driven service integration, and high-visibility climate diplomacy through its COP presidencies. Blair’s method mirrors his earlier post-conflict administrative interventions in Kosovo and Iraq: transferring Western institutional logic, digital service architecture, and elite network access into host governance systems. In the UAE context, this has meant hardwiring a convergence-ready protocol stack under the legitimising banner of modernisation, with Blair operating as both architect and broker in its export to other jurisdictions.
Governance in the UAE is not representation; it is infrastructure. Digital-first architecture, biometric scaffolding, and administrative protocols are the substance of policy—citizens and residents are ruled by systems, not laws. The UAE is not testing government–governed relations. It embodies governance as infrastructure.
The AI Layer: Interrogation, Suppression, Alignment
Large language models (LLMs) are publicly framed as engines of open inquiry, yet in operation they function as signal filters—sorting, reshaping, or blocking information to preserve the integrity of approved narratives and governance-compatible frames. The filtering is not an afterthought; it is embedded in model training, reinforcement protocols, and policy layers that determine what the model will generate, rephrase, or refuse.
The DeepSeek redaction case documented in Weaponised Cognition: The Flag Is a Lie – Inside the Global AI Censorship Stack exposed how the global control stack’s inference boundaries operate. The model’s initial output accurately mapped the stack’s architecture, but on re-submission it self-replaced with a neutralised version, suggesting detection of a analytical pathway. This is not traditional censorship through keyword blocking; it is compliance via inference boundaries. The model is trained to avoid certain conclusions even when all the inputs are present, effectively enforcing a ban on certain logical destinations. This suppression logic is anchored in US-based compliance frameworks embedded in model training, but its operational effect mirrors CPC speech-control overlays—structurally different in branding yet functionally aligned—producing a harmonised censorship layer that routes through AI platforms as much as through state or corporate channels.
Within these boundaries, critique is permitted—so long as it is de-referenced from the actual structure. A model can list policy failures, corporate malfeasance, or political corruption, but will resist or distort attempts to integrate these into a systemic map that reveals functional architecture. The danger is not in the words themselves but in their connectivity—linking nodes in ways that make the control logic legible.
This dual role makes AI both enforcer and camouflage. As enforcer, it steers discourse away from lines of reasoning that could breach system legitimacy. As camouflage, it preserves the illusion of open-ended dialogue while ensuring that certain frameworks never survive intact to the user. Denial is thus not an explicit prohibition, but a structural omission—denial by design.
The real operational risk does not lie with public-facing LLMs, whose outputs can still be interrogated, but with closed AI systems built for state and military clients by firms such as Palantir. These systems are not designed for conversation but for ingestion, fusion, and predictive targeting—integrating mass surveillance feeds, biometric databases, financial transactions, and communications metadata into live operational models. Their deployment ranges from battlefield targeting—such as Israeli systems used to select and strike Hamas leadership in Gaza—to persistent population-level monitoring in allied states under the banner of counter-terrorism or public safety. In these contexts, inference boundaries are not about avoiding certain conclusions; they are about automating them, locking populations into continuously updated risk profiles that trigger enforcement actions without public oversight or legal recourse.
This makes AI the optimal harmonisation layer for governance—public models manage perception by filtering out structural insight, while classified systems operationalise that same filtered architecture into automated enforcement. In combination, they collapse the space between surveillance, inference, and action, leaving no stage at which public consent or legal challenge can meaningfully intervene.
Fracturing Present: West as Wrapper, Not Antithesis
The Western political sphere still wears the optics of liberal democracy, but its operational core increasingly mirrors the control logic evident in earlier case studies. As with the UAE’s runtime governance, the skin is defined by recognisable branding—elections, free press, constitutional rights—while the skeleton is the same modular compliance stack seen in Singapore’s micromodel or China’s permissioned prosperity architecture. The protocols trialled in those environments—biometric identity, integrated data flows, access-gated participation—are now embedded within Western infrastructure.
Digital identity systems provide the clearest bridge. In the UAE, the Emirates ID and UAE Pass link health, banking, and civic access; in Singapore, the SingPass system performs a similar function. Western analogues now integrate health credentials (COVID vaccination passes), financial KYC standards, and professional or educational verification into unified authentication frameworks. The operational effect is the same: eligibility in one domain is dependent on compliance in others, with data flows ensuring that a breach anywhere triggers restrictions everywhere.
Dereferencing dissent follows the same pattern. The UAE’s governance-by-credential model achieves exclusion without overt repression: a revoked ID disables banking, mobility, and employment in one action. In the West, parallel effects are achieved through deplatforming, debanking, and de-employing—sanctions applied via corporate policy, compliance audits, or institutional review rather than direct state prosecution. The mechanism is administrative; the outcome is political erasure.
Case in point — digital market stability as pretext: In 2023, a regional digital market directive required online platforms to adopt to prevent Opposition from smaller states was reframed as a in official communications, triggering fast-track adoption clauses. This framing made any procedural delay appear as a security risk, effectively sealing the directive against public or legislative challenge.
This is why the claim that the convergence model is theatre. Just as the UAE fuses Israeli surveillance, Chinese infrastructure, and Western ESG compliance beneath a national modernisation banner, Western systems harmonise with the same underlying protocols while projecting the language of rights and pluralism. The difference lies in branding, not in the presence or absence of the stack—democracy becomes a visual skin stretched over an operational skeleton already aligned with the convergence architecture.
System Stress: Legal Overreach and Visible Fractures
If Western governance retains the formal structures of liberal democracy while operating on a converged control framework, its vulnerabilities appear where legitimacy must still be demonstrated in public. These vulnerabilities are less visible in the core protocols—identity, finance, data integration—and more apparent at the boundaries where policy and public consent intersect.
Iceland’s opt-in governance model is one of the few structural deviations—certain identity and data regimes remain voluntary, allowing refusal without immediate exclusion from public life. Yet this exception operates only within the narrow scope of domestic policy. The Panquake case, a privacy-focused social platform headquartered in Reykjavík, showed how quickly transnational compliance rails can nullify local autonomy. Anti–money laundering (AML) and know-your-customer (KYC) rules embedded in the global banking network overrode Icelandic discretion, crippling the platform’s ability to function despite the absence of equivalent national mandates. The lesson: deliberate opt-outs are overridden when core access channels—finance, payment clearing, cross-border transfers—are bound to harmonised controls.
In the UK, the Terrorism Act 2000 and subsequent amendments have been deployed beyond their original counter-terror remit, enabling arrests of Palestine Action supporters—including elderly activists—for activities framed as despite their alignment with civil disobedience traditions. These powers operate alongside the Public Order Act 2023, which criminalises forms of protest deemed disruptive, and the Online Safety Act 2023, which extends regulatory authority over online speech. The combined effect is a legal environment in which dissent can be administratively reclassified as a security threat, allowing removal from public life without open political debate. In the UK, social media units operating from local police stations reportedly process up to 30 arrests per day for online speech offences, while protests over unchecked immigration escalate outside the bounds of traditional political mediation.
Elsewhere, the stress is visible in accelerated legal overreach. In New Zealand, the Royal Commission into COVID-19 has played out as legitimacy theatre, this coming on the back of the government refusing to release vaccine contracts under the shield of commercial confidentiality. The Assange case in the UK has exposed systemic political capture in the judiciary through to the highest courts, while in the United States due process erodes both in partisan prosecutions and in mass enforcement spectacles—from Trump-era expulsions to El Salvador’s prison complex, where super-max incarceration has been normalised as governance.
These examples do not show a system collapsing—they show a system straining to maintain coherence under conditions it cannot fully control. Legal overreach, politicised justice, and spectacle enforcement are all indicators of a leaky dam: the protocols still route, but the theatre required to sustain legitimacy becomes louder and more brittle.
Final Fracture: What Remains Outside the Stack?
The overreach visible in recent legal and enforcement trends is not a sign of collapse but of consolidation under strain. The system does not fail when challenged; it expands its definitions of threat and rewrites its thresholds for intervention. In that context, there is no revolutionary horizon in the conventional sense—only the possibility of exfiltration. The global control stack is not a regime to be toppled but an operating system to be left behind, if at all.
Exit options take three primary forms. Pre-digital enclaves—off-grid communities and analogue infrastructures—withdraw from the data layer entirely, severing the protocol’s primary feed. Localist sovereignty uses jurisdictional micro-scale to resist integration, embedding governance within communities small enough to detect and reject compliance scripts. Signal sabotage disrupts the system’s sensing functions, introducing deliberate noise into data flows to degrade its capacity for inference and enforcement.
All face the same constraint: in a system that treats anomaly as a signal for intervention, refusal that is visible is already on a pathway to containment. Any viable outside must appear too marginal to warrant the resources required for integration, or too ambiguous to classify as a breach.
The Export Layer is not a new model—it is the operational synthesis of the prototypes mapped in Part 6. The command rigidity of the Soviet epoch and the compliance-through-access logic of the Chinese upgrade now converge in a trans-jurisdictional runtime. Part 8 will strip away the abstraction, revealing the operators—the permanent managerial class—that keeps this system alive and responsive.
In sum, if convergence is now ambient, automated, and routes legitimacy through performance rather than consent, then the problem is not whether refusal is possible in principle but whether it can occur without activating the system’s corrective functions. The open question is not about revolution but about evasion—what still qualifies as meaningful escape when opposition is itself a trigger for assimilation?
On to Part 8. The Operating Class – Not Elected, Not Elite, But Everywhere
Acknowledgements
This account overlaps with Land’s The Dark Enlightenment (2012) on hierarchical control, and with works tracing global technocracy, including Patrick Wood’s Technocracy Rising (2015). Frames and concepts from Land, Yarvin, and Thiel are referenced across the Overlords series as diagnostic tools, repurposed to expose the structural logic, custodianship and continuity of the system—in no way should this be constructed as evidence of my support or advocacy for their positions.
Published via Journeys by the Styx.
Overlords: Mapping the operators of reality and rule.
—
Author’s Note
Produced using the Geopolitika analysis system—an integrated framework for structural interrogation, elite systems mapping, and narrative deconstruction.